A Simple Example
Let's say Alice wants to send 100 USDC to Bob privately.
The Flow
- Open the Mirage app
- Enter Bob's address and the amount (100 USDC)
- Add a small tip (2 USDC) to incentivize a node to execute the transfer
- Hit send
That's it. From Alice's perspective, it feels like any other crypto transfer. But behind the scenes, something clever is happening.
Instead of Alice sending directly to Bob (which would be visible onchain and link them together), the Mirage app sets up a mechanism where someone else sends the money to Bob on Alice’s behalf. To anyone watching the blockchain, it just looks like a random address sent Bob 100 USDC. Nothing unusual or suspicious.
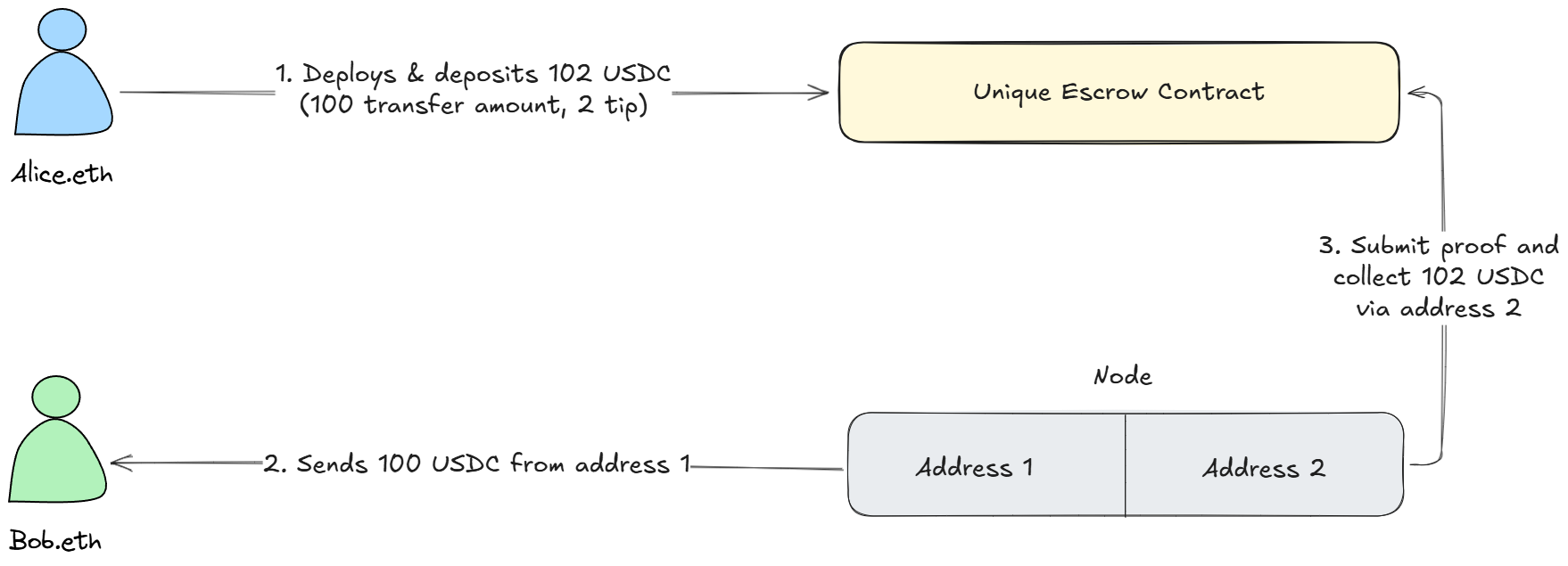
Step 1: Setting Up the Escrow
When Alice hits send, she deploys a small, temporary escrow contract through the Mirage app. This contract handles the transaction safely and privately.
- The contract looks completely ordinary. Just another contract among thousands deployed daily on Ethereum
- It's unique to Alice's transaction (not a shared pool everyone uses)
- Each deployment has small random variations in code, making it costly and unreliable to detect which contracts belong to Mirage.
Alice’s wallet deposits into this escrow:
- 100 USDC (the amount she wants Bob to receive)
- 2 USDC (a small tip to reward whoever completes the transfer)
At the same time, the Mirage app encrypts Alice’s instructions: “Send 100 USDC to Bob’s address. You’ll earn 2 USDC for doing this.” This encrypted message is then broadcast to the Mirage node network, where nodes compete to decrypt and execute it.
Step 2: A Node Picks Up the Job
The encrypted message is now floating out there, and nodes in the Mirage network are competing to decrypt it. Decryption isn't free. It requires compute resources and time. This is intentional, making it expensive for anyone to try to decrypt and analyze every message on the network.
Once a node successfully decrypts Alice's message, they see the details: "Send 100 USDC to Bob, earn 2 USDC."
If they want to take the job, here's what happens:
- The node posts a security deposit into Alice's escrow contract (ensuring they only profit by completing the job honestly)
- The node sends 100 USDC from their own wallet directly to Bob via another address
This is the key moment. Onchain, it looks like this node (some random address) is sending Bob 100 USDC. There's no visible connection to Alice. No privacy contract. No obvious privacy behavior. Just a regular stablecoin transfer.
Step 3: The Node Gets Reimbursed
The node just sent 100 USDC to Bob out of their own pocket. Now they need to get paid back from Alice's escrow contract:
- The node submits proof that they sent 100 USDC to Bob (a cryptographic proof the blockchain transaction exists)
- The escrow contract verifies the proof and confirms Bob received exactly 100 USDC
-
The contract releases payment:
- 100 USDC (reimbursement for what they sent Bob)
- Their security deposit (returned in full)
- 2 USDC (their tip for executing the transaction)
The node walks away with a 2 USDC profit. Bob has his 100 USDC. Alice has successfully sent a private payment. And to anyone analyzing the blockchain, there's no visible link between Alice and Bob, and there is no sign Alice used a privacy solution to begin with. Everything looks normal.
Why This Provides Privacy
Let's step back and look at what an observer sees when analyzing the blockchain:
Transaction 1: Alice deployed a contract and deposited some USDC into it Interpretation: Could be anything. A multisig, an MEV contract, an automated trading bot, whatever
Transaction 2: Some random address sent Bob 100 USDC Interpretation: Just a normal transfer. Happens thousands of times per day
Transaction 3: Another random address later withdrew funds from Alice's contract Interpretation: who knows?
There's no visible connection between Alice and Bob. The node's transfer to Bob looks completely independent from Alice's activity.
